Defense Department Audit Report Provides Contractors with a Roadmap to Assess and Mitigate Cybersecurity False Claims Act Risk

On December 4, the Department of Defense Office of Inspector General (DoD OIG) issued a “special” Audit Report1 (the Report) that provides insight into common cybersecurity weaknesses related to the protection of Controlled Unclassified Information (CUI). Notably, the report explains that its contents are derived, in part, from support the DoD OIG has provided to Department of Justice (DoJ) Civil Cyber-Fraud Initiative investigations. As background, the Report explains that over the 2018 through 2023 period, the DoD OIG has issued five audit reports focused on DoD contractors’ “inconsistent implementation of Federal cybersecurity requirements for protecting CUI that are contained in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171.” The Report also states that the DoD OIG has supported five DoJ investigations conducted under the auspices of the Civil Cyber-Fraud Initiative.
As noted in the Report, DoD currently has over 183,000 active contracts covering all sectors of the economy, many of which require contractors to process, store and/or transmit CUI on their own networks and systems. Through DFARS 252.204-7012, DoD requires its contractors handling CUI to implement, or have a plan to implement, the 110 security controls found in NIST SP 800-171,2 which cover a wide array of subjects, including access controls, audit and accountability, incident reporting, physical protection and risk/security assessments, among others. At a fundamental level, DFARS 252.204-7012 requires contractors to provide “adequate security” for CUI and imposes certain incident reporting obligations.
As we have discussed here, here and here, cybersecurity-centric False Claims Act (FCA) enforcement is becoming an increasing risk for government contractors and grantees, particularly since the DoJ Civil Cyber-Fraud Initiative was initiated in the fall of 2021. In light of the increasing cybersecurity-related FCA risk, the Report’s comment that its findings will assist DoD contractors and grant recipients with identifying “focus areas” prior to attesting to their compliance with NIST SP 800-171 is notable.
A. The Report’s Recommendations
The Report seeks to synthesize the findings and recommendations of its previous five cybersecurity-focused audit reports with the work the DoD OIG has undertaken in support of DoJ investigations. According to the Report, the commonalities are focused on six of the 14 NIST SP 800-171 cybersecurity categories, which are set forth in the table below (taken from the Report).
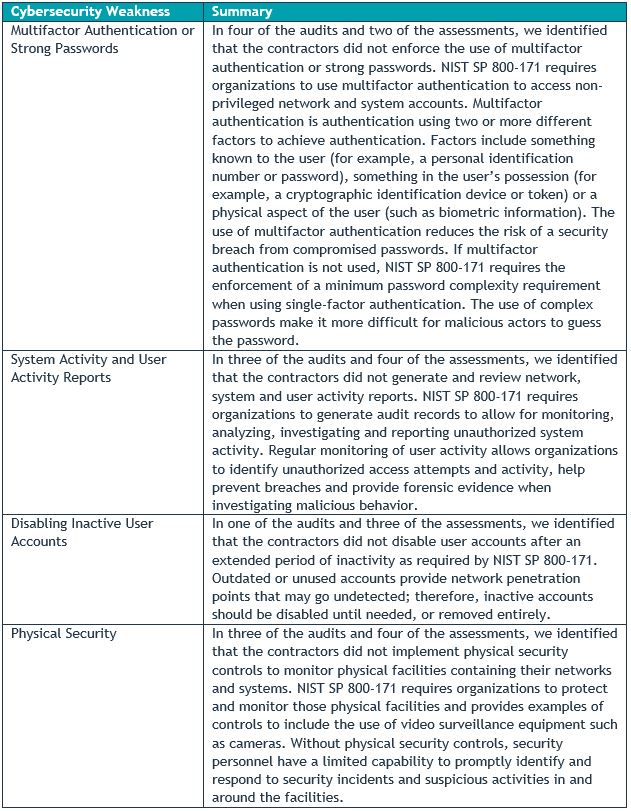
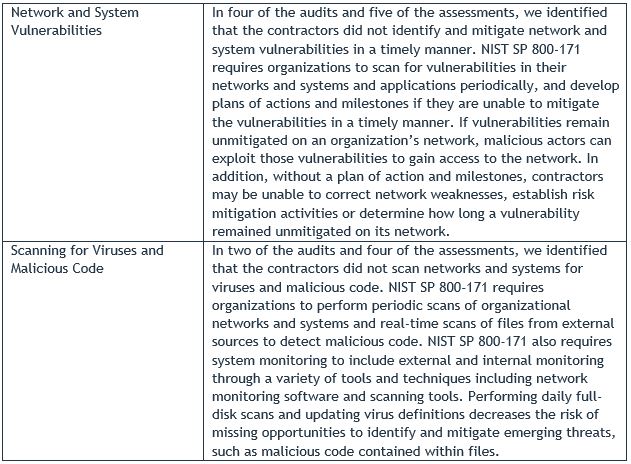
B. Key Takeaways
The relatively recently unsealed FCA case involving Penn State University3 and the Aerojet Rocketdyne settlement from July 2022 underscore the FCA risk relating to cybersecurity. Both of those matters alleged non-compliance with NIST SP 800-171 and DFARS 252.204-7012.
From a fraud risk mitigation perspective, going forward, the areas the Report identifies are likely going to be those on which contracting officers focus their contractor/grantee performance assessments, indeed the Report specifically states it will be helpful in that regard, and thus should also be areas where contractors and grantees proactively assess their compliance before making cybersecurity representations to government customers. It might also be prudent for contractors to review their current submissions in the Supplier Performance Risk System (SPRS) and consider whether there are statements that should be updated or revised.
Please contact a member of Akin’s government contracts and/or cybersecurity, privacy and data protection teams if you have any questions about how the Report may be used to mitigate your cybersecurity risk.
2 NIST SP 800-171 is currently undergoing revision. Once finalized, the new version will likely have additional and/or modified security controls. In addition, once the CMMC 2.0 rule goes into effect, and third-party assessors are required, that too will have some impact on DFARS 252.204-7012.
3 United States ex rel. Matthew Decker v. Pennsylvania State University, No. 2:22-cv-03895-PD (E.D. Pa. January 1, 2023).
4 Dept. of Justice, Press Release, Aerojet Rocketdyne Agrees to Pay $9 Million to Resolve False Claims Act Allegations of Cybersecurity Violations in Federal Government Contracts (July 8, 2022), available at https://www.justice.gov/opa/pr/aerojet-rocketdyne-agrees-pay-9-million-resolve-false-claims-act-allegations-cybersecurity.




